Activities of "nhontran"
Hi @maliming, if user is active in the site, we still need to refresh the token before expiration.
We just dont want to refresh token if user is inactive for a period of time (30 mins).
Hi @gterdem, sorry for taking too long to reply.
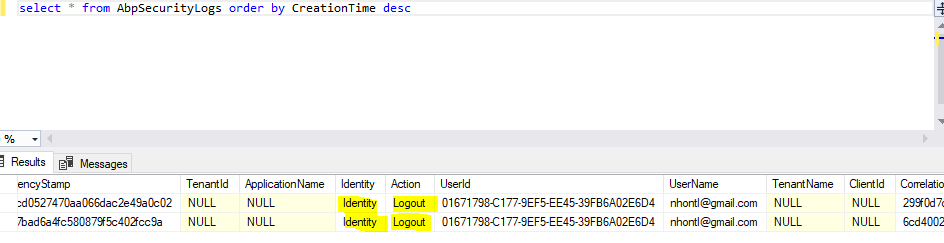
We already implemented the front-end to trigger logout if user is inactive for 30 mins and set the access token life time = 30 mins as well but it does not work for sometimes, we checked the logs and found that client side managed to call refresh token successfully.
As per Identity Server documentation, the default refresh token lifetime is 30 days: AbsoluteRefreshTokenLifetime Maximum lifetime of a refresh token in seconds. Defaults to 2592000 seconds / 30 days.
https://identityserver4.readthedocs.io/en/latest/topics/refresh_tokens.html
This client setting is not available in UI (Administration -> Identity Server -> Clients)
Is there any other way to configure it?
Hi @alper, thanks for the info.
Hi @maliming, thanks for your prompt reply, I will override this method as per screenshot, thanks.
Hi @maliming, is there any work around for this issue? we are using v.3.3.2 and dont want to upgrade to v.4.3 as it is a breaking change.
Hi @alper, will someone fix it? is there any work around for this issue?
Hi @maliming, is it for performance purpose only? what if we are using tiered project and do not install the redis? I have replaced the data protection storage provider with EF core.
Hi @maliming, why redis is mandatory for tiered project? this is not mentioned in the documentation:
https://docs.abp.io/en/abp/latest/Redis-Cache
if it is because of key storage provider, we can replace it by entity framework core, right?
https://docs.microsoft.com/en-us/aspnet/core/security/data-protection/implementation/key-storage-providers?view=aspnetcore-5.0&tabs=visual-studio
please help check and confirm.
Hi @gterdem, sorry, I have set SignInScheme to another value when doing the verification.
Your suggestion has resolved the issue, thank you very much.