Activities of "liangshiwei"
Hi,
Unfortunately, it's hard to do because it requires you to customize the ABP source code.
reason why we don't want to upgrade to latest version is we still using identity server if we upgrade to latest version we are forcing to change many things in current project.
Hi, you will not miss something. we still release the IdentityServer package.you can keep using it
Hi,
Are you using the IdentityServer or OpenIddict as a auth server? because from 6.0.0 the app template uses OpenIddict by default.
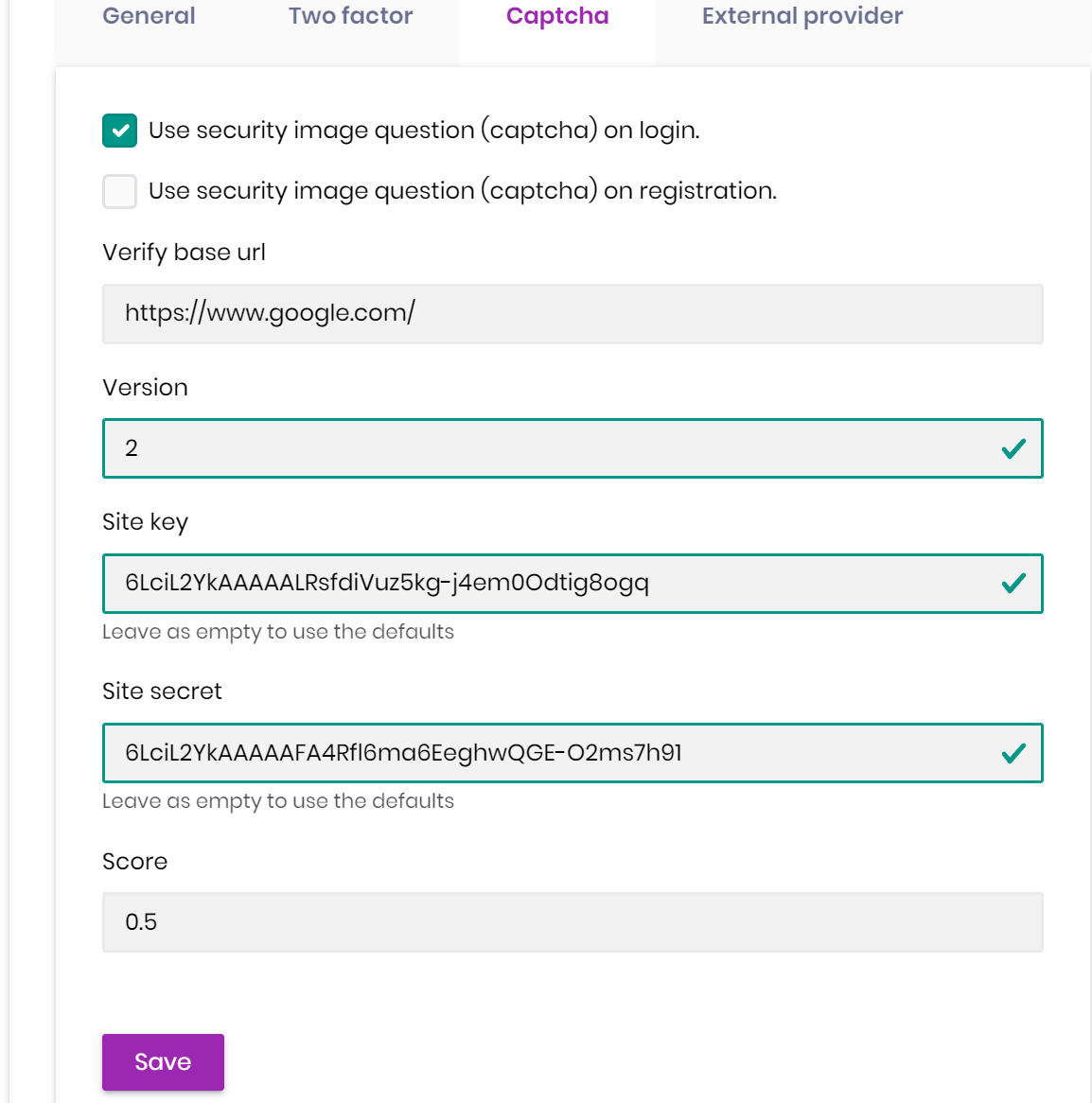
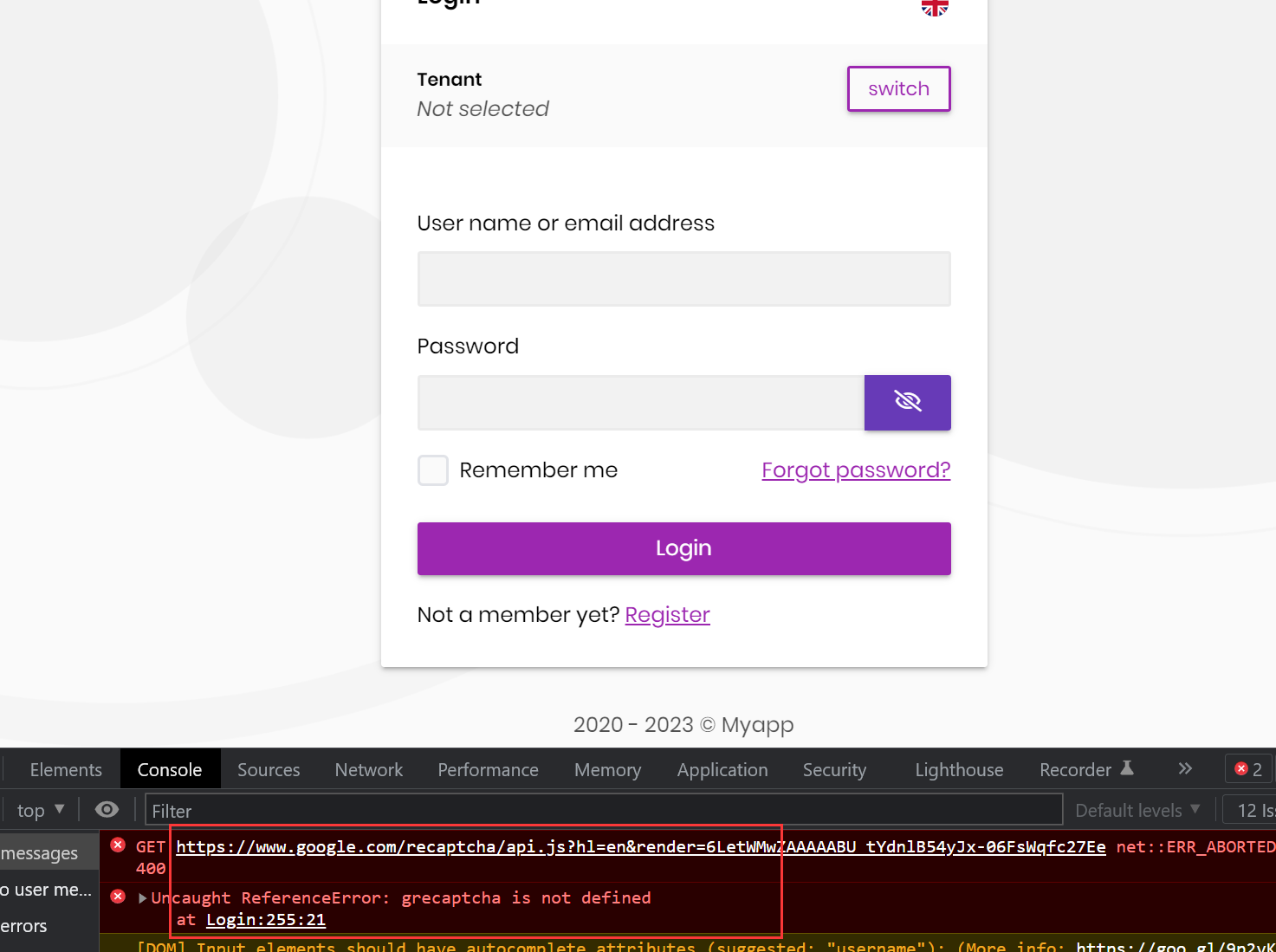
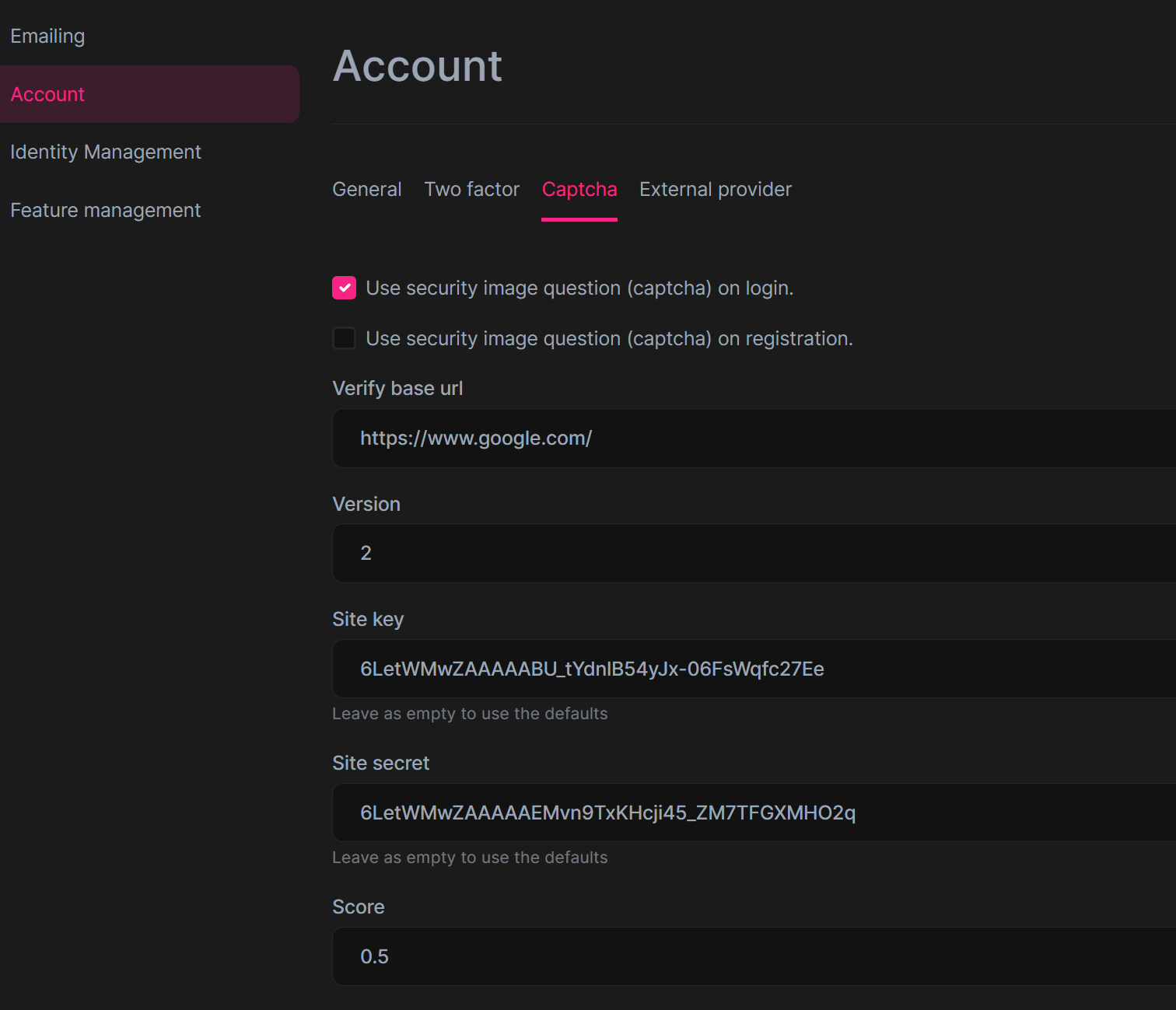
We will enhance it in the next version
Hi,
Try await serviceScope.ServiceProvider.GetRequiredService<MRSDbMigrationService>().MigrateAsync();
Hi,
You need to use the data seeding system to initial data: https://docs.abp.io/en/abp/latest/Data-Seeding
Hi,
I will check it
Hi,
Yes, it's possible, but it has a lot of work to do and breaks the existing framework design.
- Override the PermissionManagementModal to remove the
disabledproperty. - Override the RolePermissionManagementProvider
MyRolePermissionManagementProvider
[ExposeServices(typeof(RolePermissionManagementProvider))]
public class MyRolePermissionManagementProvider : RolePermissionManagementProvider
{
public MyRolePermissionManagementProvider(
IPermissionGrantRepository permissionGrantRepository,
IGuidGenerator guidGenerator,
ICurrentTenant currentTenant,
IUserRoleFinder userRoleFinder) : base(permissionGrantRepository, guidGenerator, currentTenant, userRoleFinder)
{
}
public override async Task<MultiplePermissionValueProviderGrantInfo> CheckAsync(string[] names, string providerName, string providerKey)
{
var multiplePermissionValueProviderGrantInfo = await base.CheckAsync(names, providerName, providerKey);
if (providerName != UserPermissionValueProvider.ProviderName)
{
return multiplePermissionValueProviderGrantInfo;
}
var permissionNotGrants = await PermissionGrantRepository.GetListAsync(names, providerName, $"{providerKey},False");
foreach (var permissionNotGrant in permissionNotGrants)
{
if (multiplePermissionValueProviderGrantInfo.Result.ContainsKey(permissionNotGrant.Name))
{
multiplePermissionValueProviderGrantInfo.Result[permissionNotGrant.Name] = new PermissionValueProviderGrantInfo(false, providerKey);
}
}
return multiplePermissionValueProviderGrantInfo;
}
}
It will check the user permissions again and change the result if the permission is not granted to the user.
- Override the UserPermissionManagementProvider
MyUserPermissionManagementProvider
[ExposeServices(typeof(UserPermissionManagementProvider))]
public class MyUserPermissionManagementProvider : UserPermissionManagementProvider
{
protected IUserRoleFinder UserRoleFinder { get; }
public MyUserPermissionManagementProvider(IPermissionGrantRepository permissionGrantRepository, IGuidGenerator guidGenerator, ICurrentTenant currentTenant, IUserRoleFinder userRoleFinder) : base(permissionGrantRepository, guidGenerator, currentTenant)
{
UserRoleFinder = userRoleFinder;
}
public override Task<MultiplePermissionValueProviderGrantInfo> CheckAsync(string[] names, string providerName, string providerKey)
{
var key = $"{providerKey},True";
return base.CheckAsync(names, providerName, key);
}
public override async Task SetAsync(string name, string providerKey, bool isGranted)
{
if (isGranted)
{
await RevokeAsync(name, $"{providerKey},False");
if(await ShouldAddPermissionAsync(name, providerKey))
{
await AddIfNotExistsAsync(name, providerKey, isGranted);
}
return;
}
await RevokeAsync(name, $"{providerKey},True");
await AddIfNotExistsAsync(name, providerKey, isGranted);
}
private async Task<bool> ShouldAddPermissionAsync(string name, string providerKey)
{
var userId = Guid.Parse(providerKey);
var roleNames = await UserRoleFinder.GetRolesAsync(userId);
foreach (var roleName in roleNames)
{
var permission = await PermissionGrantRepository.FindAsync(name,RolePermissionValueProvider.ProviderName, roleName);
if(permission != null)
{
return false;
}
}
return true;
}
private async Task AddIfNotExistsAsync(string name, string providerKey, bool isGranted)
{
var key = $"{providerKey},{isGranted}";
if (await PermissionGrantRepository.FindAsync(name, Name, key) != null)
{
return;
}
await PermissionGrantRepository.InsertAsync(
new PermissionGrant(
GuidGenerator.Create(),
name,
Name,
key,
CurrentTenant.Id
)
);
}
}
It will add suffixes True and False to the provider key.
It should work for you, but I didn't consider all scenarios. you should do the full test to check it and enhance it