Activities of "gterdem"
5.3 final release ?
It is under Q&A test right now. There are lots of upgrades related to multi-tenancy. If tests are succeeded, these updates will be released in 5.3 final.
It is used for User Permissions. When you try to grant permission to user, AdministrationService makes a request to IdentityService.
There is no user in server-to-server interactions hence there is no user claims to customize.
For adding custom claims you can check the answers from these issues:
- https://support.abp.io/QA/Questions/930/Create-custom-claims-and-add-them-to-ICurrentUser--ICurrentPrincipalAccessor
- https://support.abp.io/QA/Questions/1190/Adding-Custom-Claims-to-the-Logged-in-User
- https://support.abp.io/QA/Questions/1013/How-to-customize-claims
If you are asking for how to integrate custom mobile application to identityserver, it is out of ABP scope. As much as I would like to help, I have no expertise on this subject..
You can check the links i have provided in this answer.
As I deployed microservices on Kubernetes, Do I need to follow Kubernetes ocelot configuration as per below? https://ocelot.readthedocs.io/en/latest/features/kubernetes.html
Did you use the ocelot kubernetes library? It shouldn't be necessary.
[07:08:41 INF] Failed to validate the token. Microsoft.IdentityModel.Tokens.SecurityTokenInvalidIssuerException: IDX10205: Issuer validation failed. Issuer: 'https://auth-server-v1.order-line.co.uk'. Did not match: validationParameters.ValidIssuer: 'null' or validationParameters.ValidIssuers: 'http://auth-server-v1.order-line.co.uk'. at Microsoft.IdentityModel.Tokens.Validators.ValidateIssuer(String issuer, SecurityToken securityToken, TokenValidationParameters validationParameters)
It happens because the issuer is automatically set by the request. Set issuer to fix this problem In AuthServerModule.cs as follows:
Configure<IdentityServerOptions>(options =>
{
options.IssuerUri = configuration["App:SelfUrl"];
});
Assuming you override App:SelfUrl with https://auth-server-v1.order-line.co.uk
I have changed the ocelot values in config map with the service's endpoint address and the above issue is fixed but is this the correct configuration to use the service endpoint instead of the domain URL in the production?
Yes, api gateway should re-route to internal network instead of over-internet.
You can use IdentityServer Management UI and save your mobile application to identityserver and give necessary permissions. Here is a guide for server-to-server communication configuration for microservices. This is the case when you are trying to make a request from a console application to an API.
This is out of ABP scope but you can check these links for better understanding and implementation: https://stackoverflow.com/questions/43121401/how-to-use-identity-server-4-sign-in-with-desktop-mobile-apps https://cuteprogramming.wordpress.com/2018/07/14/connecting-android-app-with-identity-server-4 https://damienbod.com/2019/02/20/asp-net-core-oauth-device-flow-client-with-identityserver4
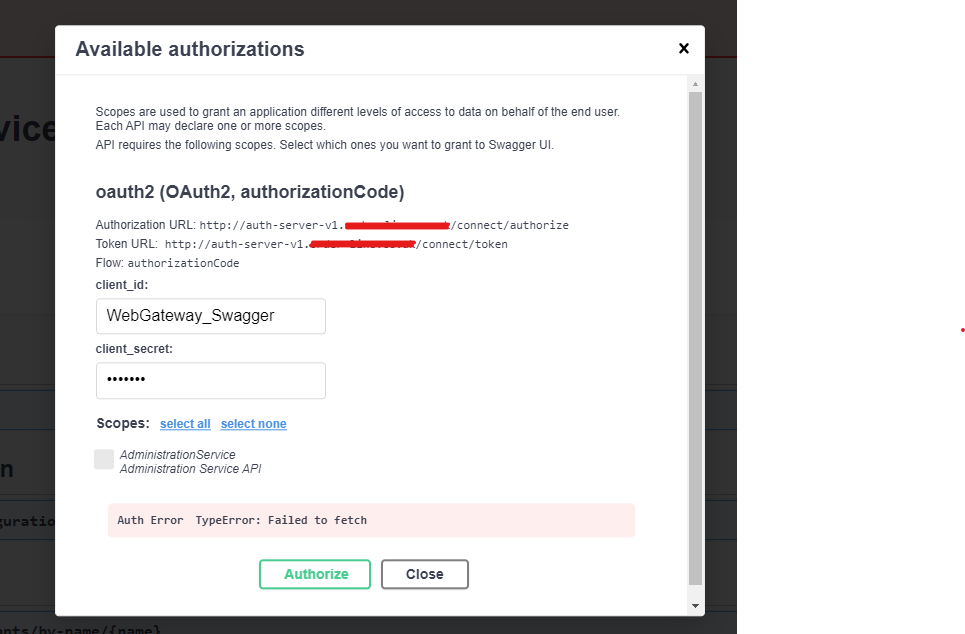
I checked with http as well but I am getting following error in swagger when try to authorise.
Can you please provide your email so I can share all domain details with you?
Sure, please email to info@abp.io
SSL connection could not be established, see inner exception. ---> System.IO.IOException: Cannot determine the frame size or a corrupted frame was received.
It seems you are re-routing to HTTPS in a gateway. This is an internal network. The request should be redirected to a microservice hosted pod/container using HTTP (port 80 instead of 443).
We are using angular for presentation, not Mvc. Our security scanner is reporting some Mvc pages under Manage to have security issues. We think we can route to these pages because of the call to this method:
If you share your security reports, we can help better.
is there a way we can remove routing to the Manage pages? When we remove the line above, the site is broken. We think the routing to our webapi is also being preformed by the method
The account module is managed by IdentityServer and it is hosted by the backend application. That's why you are redirected back to the backend for account-related operations.